Setup
Create a trail in AWS CloudTrail
AWS CloudTrail is a service that helps you enable governance, compliance, risk auditing, and operational auditing of your AWS account. Actions taken by a principal (typiclally a user, role or AWS service) are recorded as events in CloudTrail.
To learn more about CloudTrail you can click on this link. Documentation on creating a Trail via the Console is located here.
For today’s lab, we will require a new trail to be created.
- Search for the CloudTrail service under the Management Tools Section in the console and click on CloudTrail.
- Click on Getting Started (if presented with that screen). Once in the CloudTrail Console, click on Trails on the Left Side of the screen.
- Then click on Create trail to create our trail for this lab.

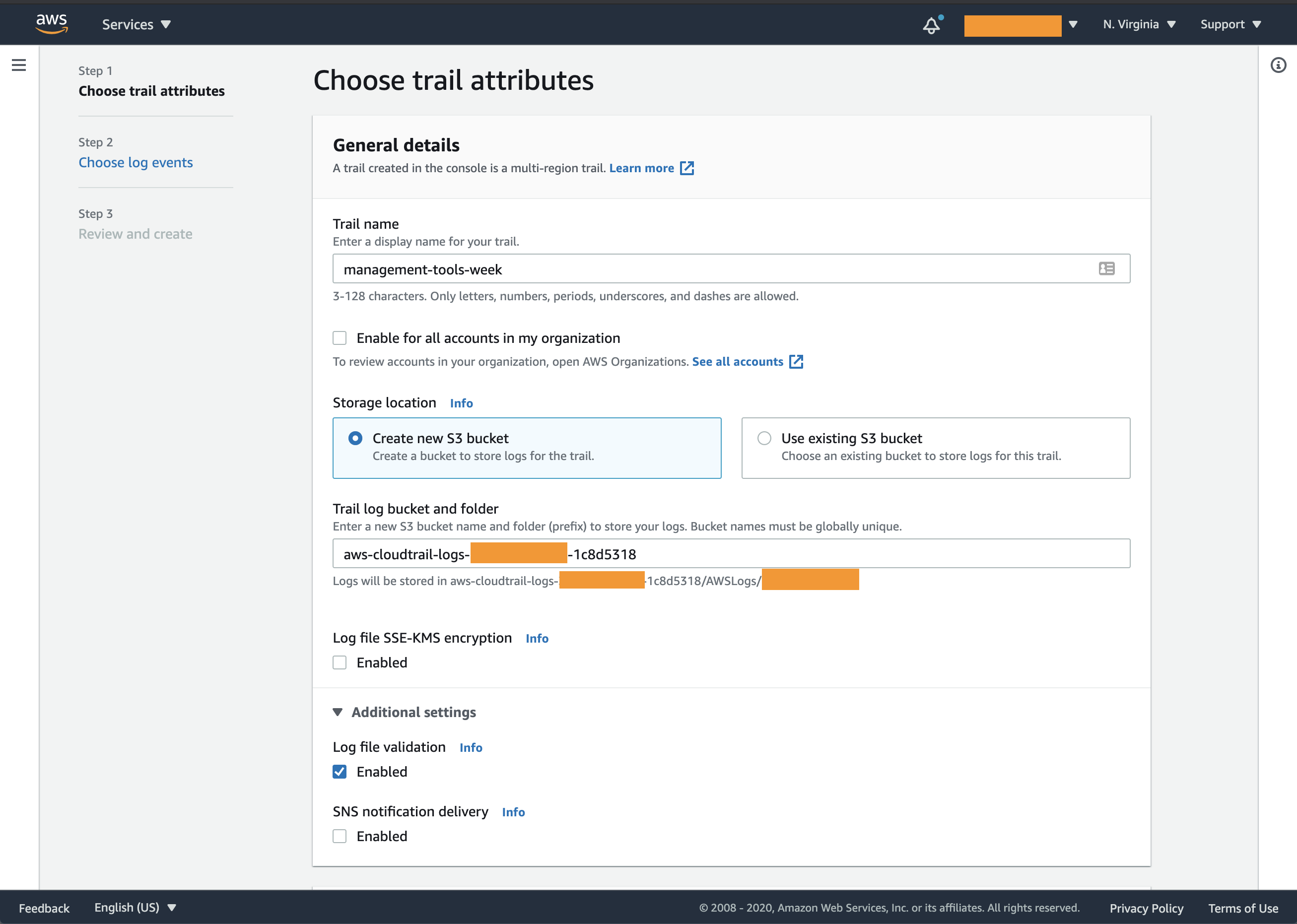
- Apply the following settings to the trail:
- Trail name: management-tools-week
- Storage location: Create new S3 bucket (default)
- Trail log bucket and folder: leave untouched
- Log file SSE-KMS encryption: unchecked
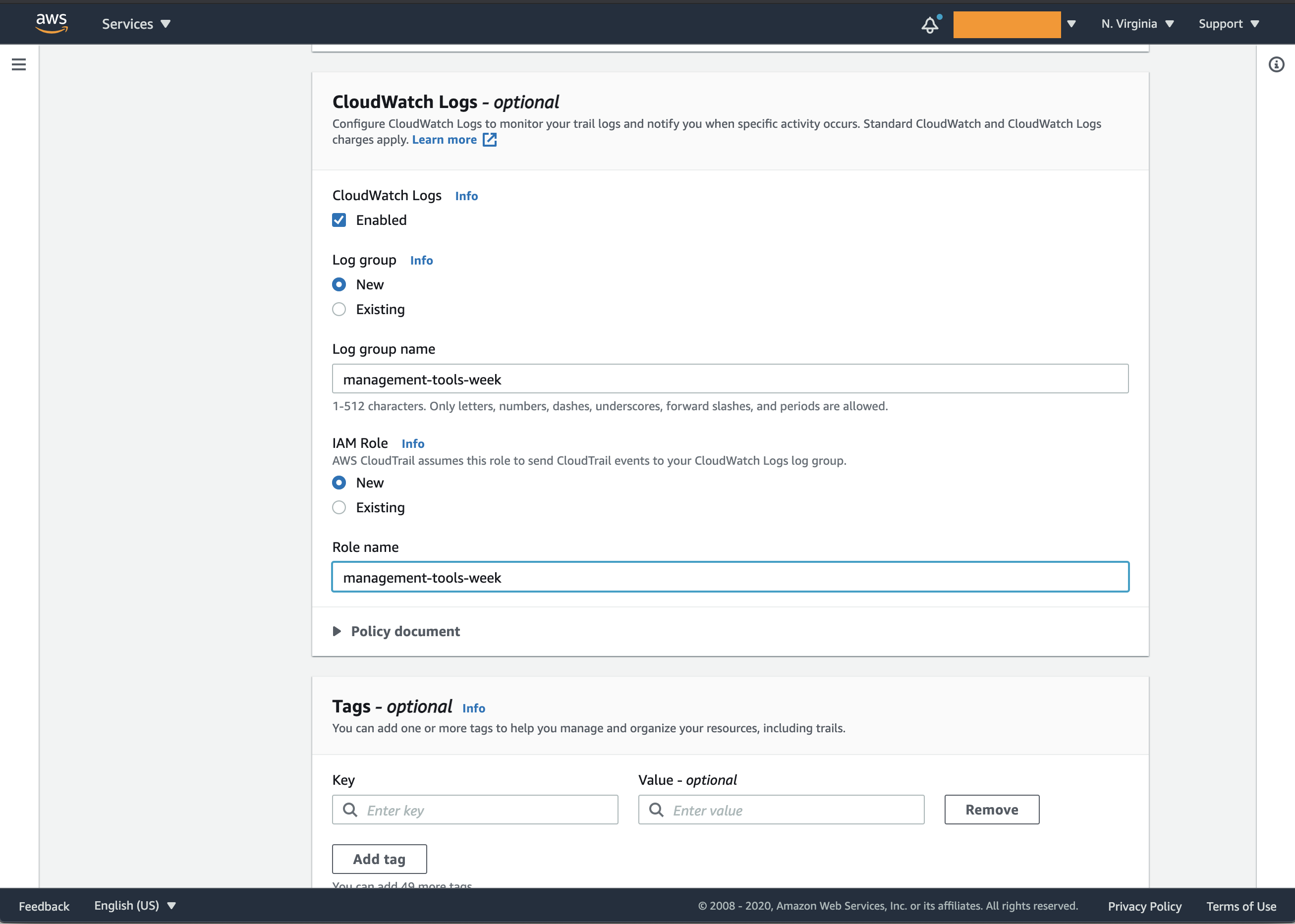
- CloudWatch Logs: enabled
- Log group name: management-tools-week
- IAM Role: New
- Role name: management-tools-week
- Click Next to proceed to the next step
- Click Create trail to complete the process
We now have a trail capturing activity in our AWS Account. Later on, we will search through our trail to reveal details about our account activity and modifications to our resources.
Activate Config
Config provides a detailed view of the configuration of AWS resources in your account. This includes how the resources are related to one another and how they were configured in the past so that you can see how the configurations and relationships change over time.
Config is a regional service. The region where you enable this service must be consistent throughout the labs, otherwise you will have a broken experience. Be sure that the region you perform this operation in remains unchanged throughout the day.
- Search for the Config Service under the Management Tools Section in the console, and then click on Config.
- Click on Get started, and we will follow the setup wizard.

- On the Settings page make the following selections

- Record all resources in this region
- Include global resources
- Create AWS Config service-linked role
- Create a bucket (and accept the default bucket name)
- Click Next on the next screen, bypassing rule selection. We will setup Config rules in the next steps.
- On the last screen click on Confirm.
We now have AWS Config recording changes for supported resources, and you can proceed to Config rule with remediation.